With the recent software update to Android Marshmallow being rolled-out to BlackBerry PRIV owners, the good news also extends to BlackBerry Developers as we’re thrilled to share the developer release of BlackBerry Integrity Detection!
What is BID
It’s like a personal security guard for your smartphone, exclusive to the BlackBerry PRIV.
Technically speaking, BlackBerry Integrity Detection (BID for short) is a trusted/secure background process running at the system level, that monitors the device for known security vulnerabilities. The BID service has its definitions updated regularly (silently) to ensure that you’re protected against existing and future exploits.
When you combine this with BlackBerry’s aggressive OS patching strategy, our choice to embed security into our hardware and DTEK’s customization, it’s clear how BlackBerry’s Android is second-to-none for security and privacy.
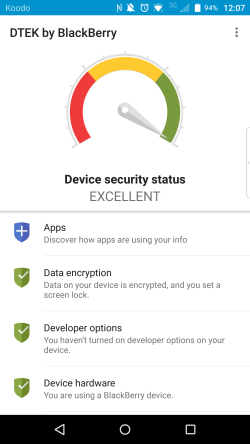 DTEK by BlackBerry app
DTEK by BlackBerry app
BlackBerry PRIV users are already familiar with the BID engine running on their devices, albeit unknowingly, since the popular DTEK app has been leveraging the BID framework since launch. Now, with the update to Android 6.0 (Marshmallow/API23), the same service providing data to DTEK is also being made available to BlackBerry Developers targeting PRIV.
When to use BID
The BID background system process is always running in the background to keep an eye out for your security and privacy via DTEK. Now, third-party developers can run their own BID reports just prior to instances where security is absolutely paramount, to ensure that the device is not compromised and running as securely/privately as possible. Some suggested scenarios where a developer would choose to run a BID report would be prior to:
- Prompting a user for their login credentials (sample)
- NFC Transaction (data transfer, mobile payment) (sample)
- Device unlock screen
- MDM/EMM monitoring
- Invoking another app or Intent filter
- Connecting to a WiFi hotspot
The BID framework allows developers to add an additional layer of security to protect themselves, and their user-base, in the event of an (attempted) security breach. This is particularly valuable in a BYOD scenario where enterprise administrators can’t trust what end-users have done to their device.
How integrate your app with BID
The BID framework is made available as an on-device library, meaning that a physical device would be required for testing/debugging purposes. The BID engine is exposed to developers via the standard Android ContentHandler API. This architecture was chosen to reduce development overhead (no additional SDK) and allow you to integrate BID as quickly and easily as possible.
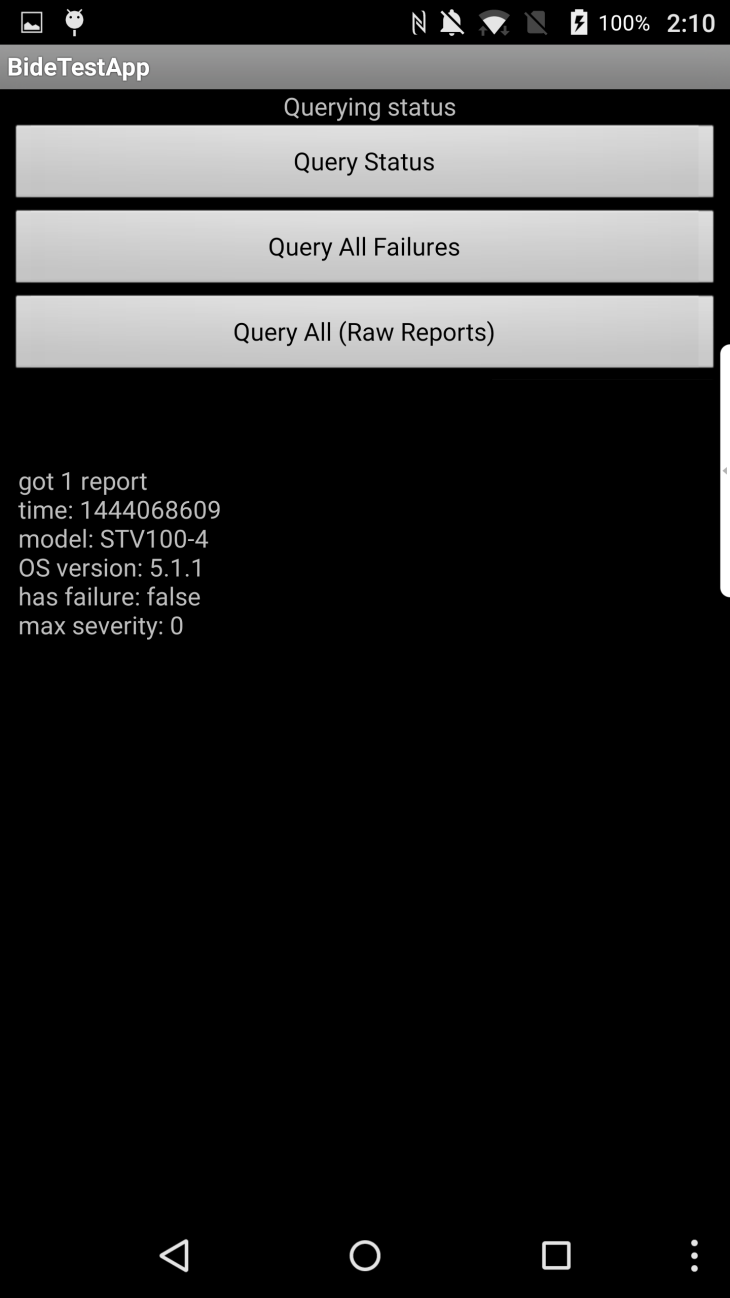 Examples of the ContentHander calls made available to expose BID functionality include:
Examples of the ContentHander calls made available to expose BID functionality include:
content://com.blackberry.bide/reports
- Return a table representing the last failed report that BlackBerry Integrity Detection captured since the device came up out of factory state
content://com.blackberry.bide/reports?id=2f550e79
- Specify a failed report
content://com.blackberry.bide/status
- Generate a new BlackBerry Integrity Detection report containing the nonce specified by the 3rd party
- BID reports indicate whether any compromises have been detected since the device was last wiped
- Demonstrates BlackBerry Integrity Detection stack is alive
- Report is generated on the fly, not saved in BID’s database
Verified, Encrypted Reports
The BID reports that are returned are secured using military grade-encryption, in order protect their integrity from possible man-in-the-middle attacks.
Throughout the private developer beta program that was run for BID, the feedback received from our (awesome) development partners was consistent in how easy integration was and the ROI. A special thanks goes out to our participating developers in helping us to harden this offering!
Developer Resources
Feel free to leverage the sample applications that we’ve made available within our BlackBerry Developer GitHub repository. There are two particular use-cases that we’ve integrated BID within:
- BidLogin, prior to asking a user for their login credentials, as well as
- BidNFC, before an NFC transaction takes place.
We’ve also published two technical papers surrounding BID within our BlackBerry Developers Knowledge Base section which outline BID Usage and BID Overview.
Additionally, you can decrypt BID reports using the Bouncy Castle encryption library, which is distributed via the MIT license.
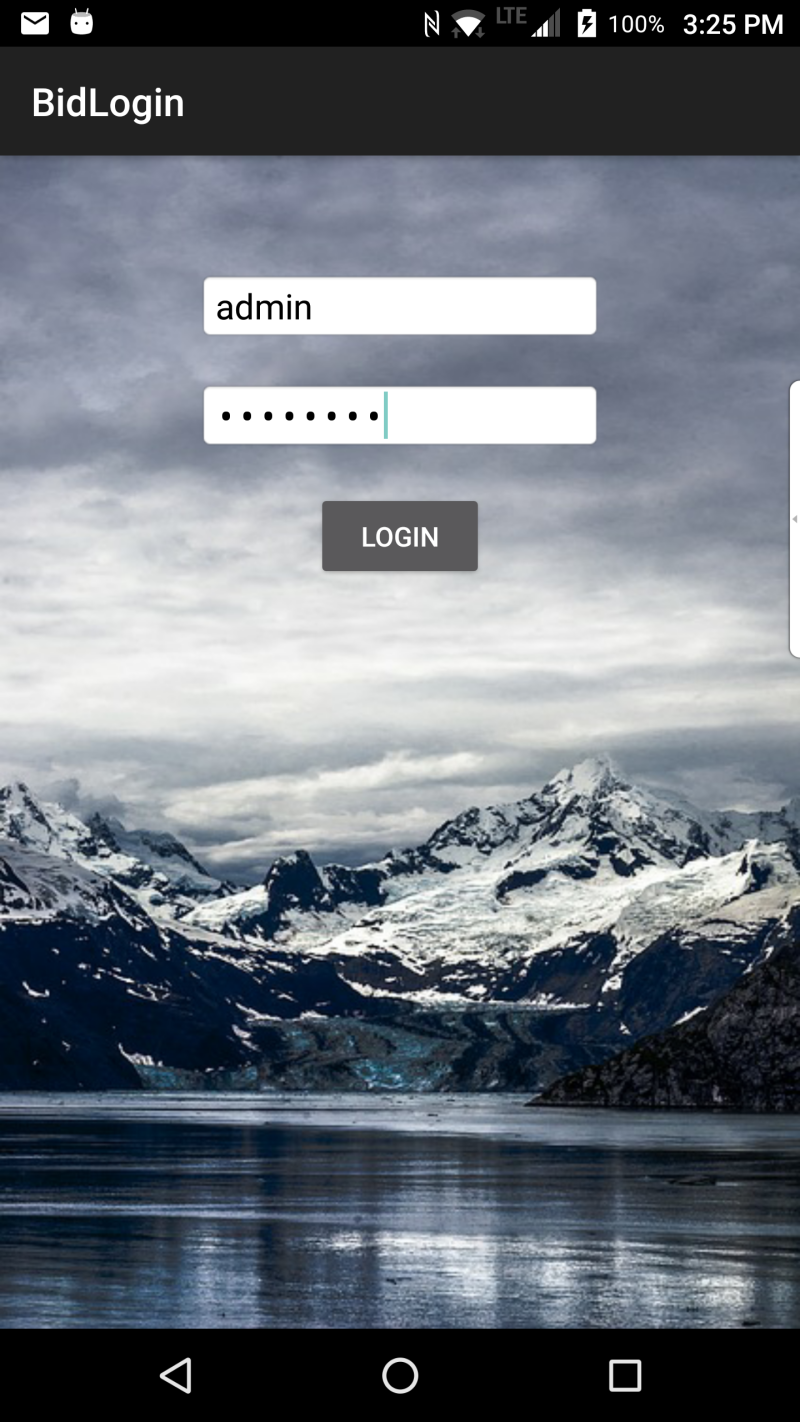

BIDLogin and BIDNFC sample applications.
We’re thrilled to see how developers will integrate BlackBerry Integrity Detection into their existing apps to add a layer of security, or even create brand new apps which are based-on BID. Feel free to share your ideas below on how you think developers can integrate this security feature into new or existing Android apps for BlackBerry PRIV.